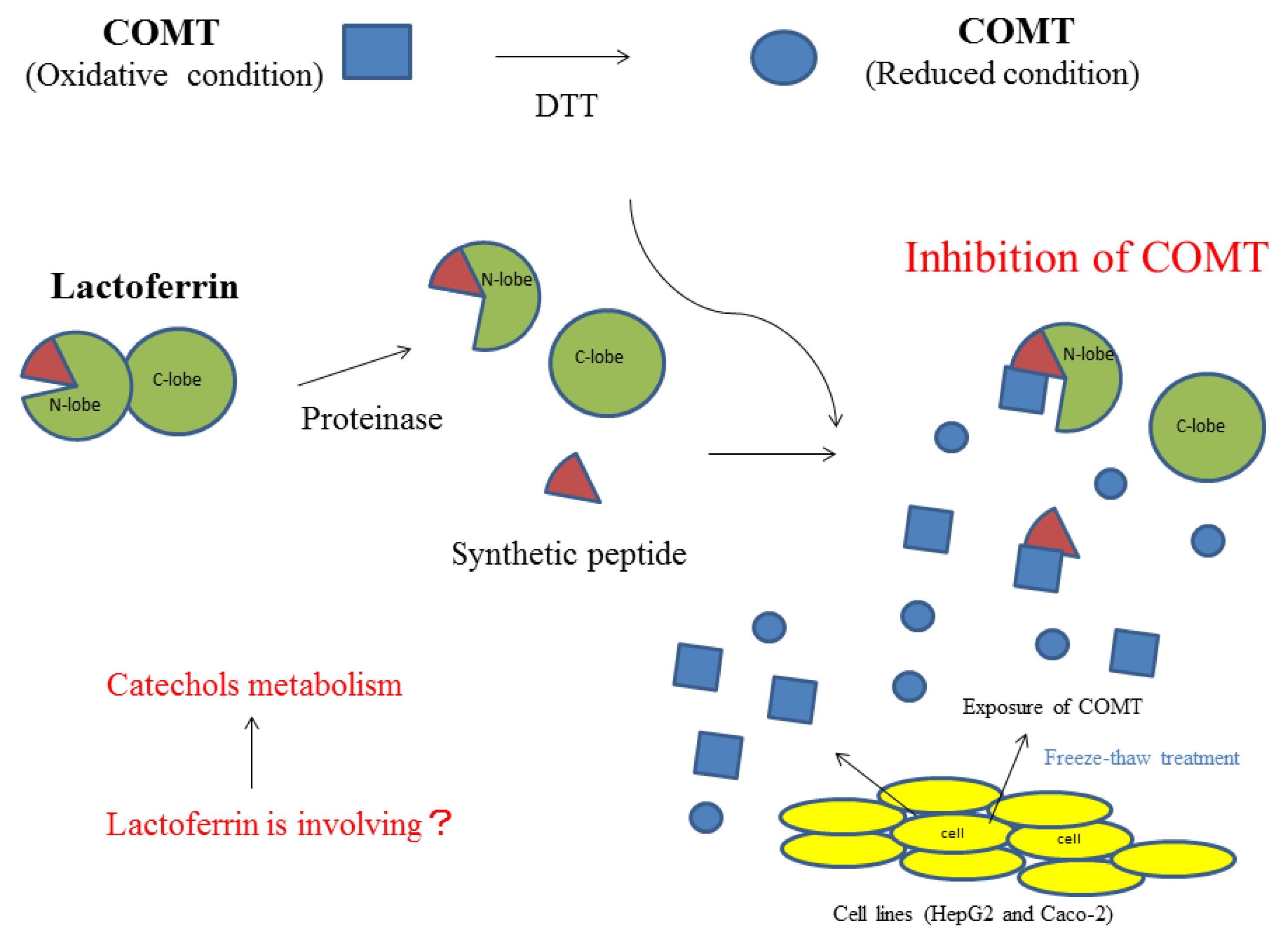
We protect your personal information by using data security technology and using tools such as firewalls and data encryption.
Blf/Terms Of Use/
We protect your personal information by using data security technology and using tools such as firewalls and data encryption....